We'll be looking at a tryhackme room called MrPhisher so it says that i received a suspicious email with a very weird looking attachment it keeps on asking me to enable Macros what are those so this straight away gives us a hint that we are going to deal with Macros So, Macros is a type of scripting language that you know you can embed in a excel or a word file so that it can even try to automate things to an extent so nothing challenging it just says that files you need are located in the home ubuntu MrPhisher on virtual machine and i have the vm(virtual machine) open up right here.
When we start the machine, we found two files in home directory. “MrPhisher.docm” is a document with the ability to run macros and the zip file has the same file but compressed.
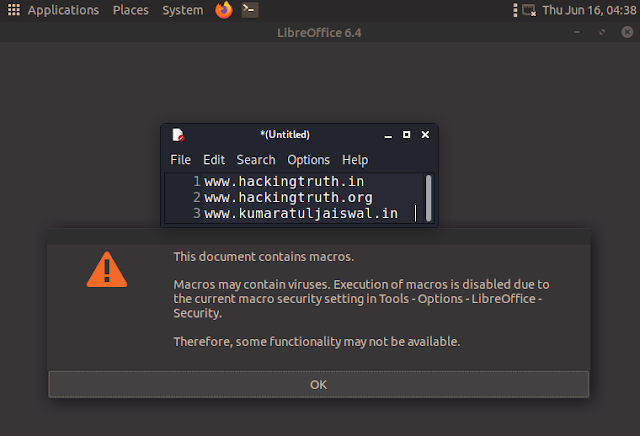
If we try to get open the file, we see the document indeed contain macros.
The document shows this one image.
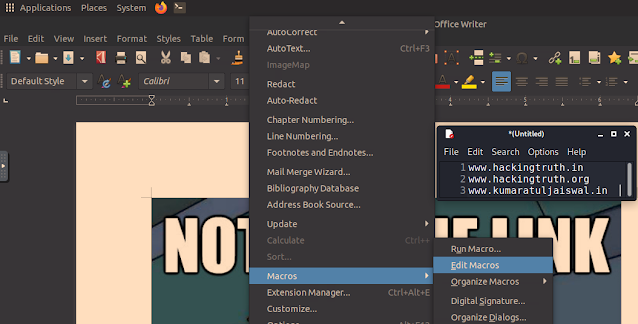
Now, to view and edit macros using Libre Office, go to Tools menu, choose Macros > Edit Macros. This opens a list of macros available in the currently open document.
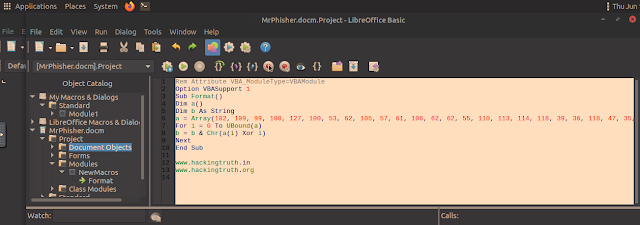
This macro contains a visual basic script...
If you want copy this file in your loca;l machine then you can try this with netcat, To make easy the analysis and be able to download needed tools, I transferred the file to my local machine with netcat.
Local machine:
nc -nlvp <PORT> > MrPhisher.docm
Remote machine:
Setting listener and getting file.
nc <IP> <PORT> < MyPhisher.docm
As a note, is important to verify the integrity of the transferred file, in previous images you can see I checked MD5 hash, and it’s the same.
via md5sum
md5sum MrPhisher.docm
But we will use into vm direct.. this code is here...
Rem Attribute VBA_ModuleType=VBAModule
Option VBASupport 1
Sub Format()
Dim a()
Dim b As String
a = Array(102, 109, 99, 100, 127, 100, 53, 62, 105, 57, 61, 106, 62, 62, 55, 110, 113, 114, 118, 39, 36, 118, 47, 35, 32, 125, 34, 46, 46, 124, 43, 124, 25, 71, 26, 71, 21, 88)
For i = 0 To UBound(a)
b = b & Chr(a(i) Xor i)
Next
End Sub
Three things are done here:
- XOR operation is done with a value and it's index in the array.
- The result of this operation is converted to a character.
- This character is appended to a string. The resulting string is a flag for this challenge.
I wrote a Python script to solve this challenge. The code can be found down below.
#! /usr/bin/env python3
# Values array
a = [102, 109, 99, 100, 127, 100, 53, 62, 105, 57, 61, 106, 62, 62, 55, 110, 113, 114, 118, 39, 36, 118, 47, 35, 32, 125, 34, 46, 46, 124, 43, 124, 25, 71, 26, 71, 21, 88]
# Array to store letters
flag = []
# Do XOR operation with a value and it's index
for i in range(len(a)):
flag.append(chr(a[i] ^ int(i)))
# Join letters to a word
print("".join(flag))
Lets Run
ubuntu@thm-mr-phisher:~/mrphisher$ nano hackingtruth-oledump.py
ubuntu@thm-mr-phisher:~/mrphisher$ nano hackingtruth-oledump.py
ubuntu@thm-mr-phisher:~/mrphisher$ nano hackingtruth-oledump.py
ubuntu@thm-mr-phisher:~/mrphisher$ python3 hackingtruth-oledump.py
flag{a39a07a239aacd40c948d852a5c9f8d1}
ubuntu@thm-mr-phisher:~/mrphisher$ #hackingtruth.org
ubuntu@thm-mr-phisher:~/mrphisher$ #hackingtruth.in
ubuntu@thm-mr-phisher:~/mrphisher$
Done.